Cybersecurity
Overview
It is a fact that Industrial and control systems are more and more vulnerable to cyber attacks due to their modern design:
-
They use commercial technologies.
-
They are more and more connected.
-
They can be remotely accessible.
-
Their strategic location in the industrial processes is a point of interest for hackers.
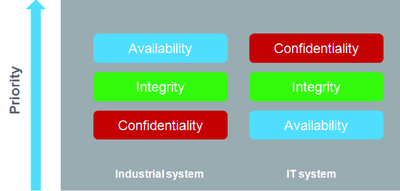
Industrial systems have also different cyber security objectives compared to typical IT systems. To secure properly the industrial installation, it is important to understand these differences. Three fundamental characteristics have to be considered:
-
Availability of the system: how to ensure that the system remains operational?
-
Integrity of the data: how to maintain the integrity of information?
-
Confidentiality: how to avoid information disclosure?
The priorities between an industrial system and a typical IT system are not the same as described on the following diagrams:
A good recommendation to address these security objectives is to adopt a defense-in-depth approach matching these priorities.
To help
keep your Pro-face products secure and protected, we recommend that you implement
the cybersecurity best practices. Following the recommendations may
help significantly reduce your company’s cybersecurity risk.
For the recommendations, refer to the following URL.
https://www.pro-face.com/trans/en/manual/1087.html
This product requires the sign-in password to be set in order to reduce the risks of unauthorized access, intrusion and infection of malicious software. Refer to At First Startup.
| Phase | Setup phase | Operation phase | Maintenance phase |
| Authority | Administrator account | User account | Administrator account |
Use this product in an environment that takes into account the above items to reduce security risks.